Building a network backbone
Network as a Service#
Fundamental to any network that includes mulltiple sites, cloud interconnects, central security, internet access, or central hosting, is a network backbone.
Spine and leaf topology#
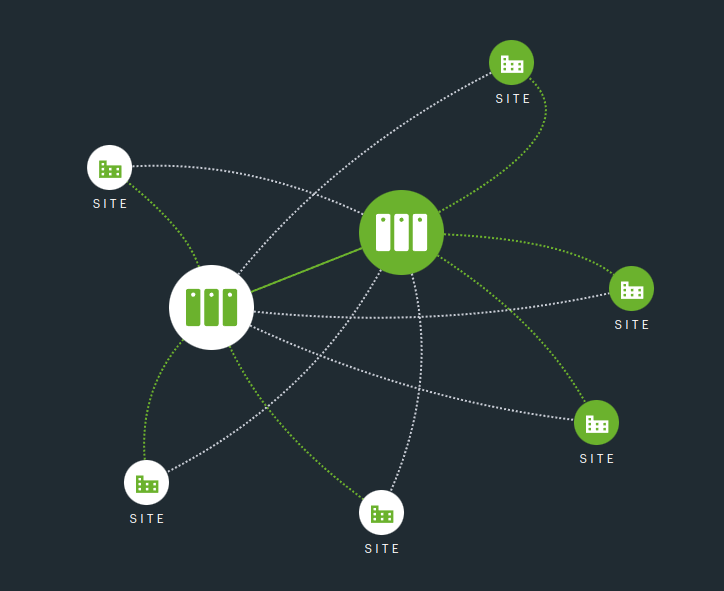
When a network backbone is created, it is always in a spine and leaf topology with the edge appliances that connect to it.
Each EVX connects to at least 2 Network Fabric Routers (NFR) across two geographically distinct datacentres for resiliency and flexibility purposes.
Connecting services to the network backbone#
The most basic network backbone is purely there to augment, aggregate and improve the quality of the connectivity of the sites connected to it. So purely site to site traffic, with no internet, much like a traditional MPLS network.
But once that is established, additional destinations can be connected. The most common is internet access, where an amount of bandwidth is chosen for each datacentre, and public routed IPs are applied (whether centrally or locally depending on the desired network topology and security posture).
It doesn't end at internet bandwidth though, as other interconnects to either third party datacentres, cloud providers, other legacy networks can be added, so that one or more sites on the WAN can have access to one or more of them.
VPN connections instead of interconnects#
VPNs can also be established in place of physical interconnects, using the internet bandwidth provisioned. Again this is possible with 3rd party datacentres, cloud security providers and the big cloud hyperscalers in order gain access to other resources or services.
These VPNs would be connected to the network backbone, so that again, any site can have access centrally, and with redundancy.
Backbone hosting#
Because the network backbone exists within physical datacentres, additional servers and appliances can be hosted right at the centre of the WAN.
Whether colo, or dedicated servers, firewall or filtering appliances, a customised network backbone that includes app hosting and centralised security immediately cuts the costs of providing interconnects and bandwidth to those elements when hosted elsewhere.
Sites connect to the network backbone, and so placing as much in that location as possible shortens the network distance, cuts the costs of provisioning and take potentially expensive or unreliable on premise or cloud hosted elements and brings them to the heart of the network, with datacentre grade power and security.
Central security#
You may only have a handful of sites and so edge firewalls may make sense, but there is always a tipping point in terms of management and cost that makes a centralised approach more appealing.
Putting the firewall cluster in the network backbone doesn't lengthen or shorten the network distance that end users traverse to get to the internet compared to edge firewalls, but a single high powered cluster gives greater control, lower licencing costs and a simpler topology.
Remote worker VPNs#
The network backbone is also the logical place to put VPN endpoints for remote access to the resources on the WAN. Whether part of a general security firewall cluster, or dedicated hardware, client VPNs can connect to the network backbone before traversing whatever other network connectivity has been provisioned to access resources, whether on premise, in the cloud, or hosted centrally in the backbone. Once on the network backbone, users can be treated identically to if they were sat at an edge site.